Microsoft Live Response - command injection/RCE
What is "Live response"
From Microsoft Docs
Live response gives security operations teams instantaneous access to a device (also referred to as a machine) using a remote shell connection. This gives you the power to do in-depth investigative work and take immediate response actions to promptly contain identified threats in real time.
Live response is designed to enhance investigations by enabling your security operations team to collect forensic data, run scripts, send suspicious entities for analysis, remediate threats, and proactively hunt for emerging threats.
The Live Response console, is basically a restricted Powershell shell with its own commands. Depending on the role that's been granted to you, you can run basic or advanced live response commands. The "basic commands" are very restricted, but the "advanced commands", give you ability to upload Powershell-scripts to a repository and run them on any computer you connect to. The console runs in the context of "NT System", so you can imagine the impact if an account with Advanced commands rights got compromised.
The problem here, is that you probably want members of your security operations team to have the ability to run scripts, like if you have uploaded a script-toolkit to your repository. But one should also keep the number of users that can upload new scripts to a minimum.
To further secure the environment and accomplish this, one should only allow digitally signed scripts. (this is the default setting and should not be disabled). This way you can upload a script-toolkit to the repository and allow every member of your team run them, but only scripts signed with a trusted signing certificate (limit access to those certificates of course) may upload a executable script.
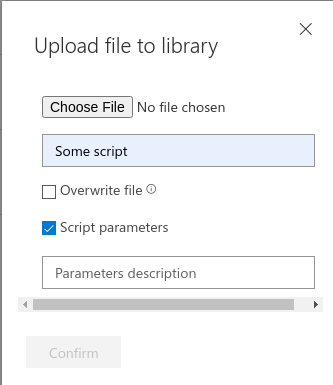
Sometimes you need to be able to pass parameters to script too. Microsoft Live Response allows this, by letting you tick "Script parameters" when uploading. This marks the script as a parameter-script and you can pass parameters to it when running it.
What I found was that you could inject commands into the parameter. Like so:
"'parameter';Command"
This would then execute any command added. In the example below, executing
whoami
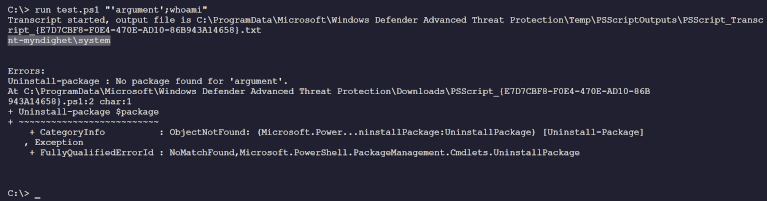
I even managed getting a Powershell Reverseshell from one of our servers.
This meant that if an account with rights to run scripts would be compromised, the attacker could run any command on any computer/server as the nt-Authority\System account.
Complete local domain pwnage from the cloud!
I reported this to Microsoft Security Response Center. I responsibly waited for them to address this before disclosing and they now reported back that the issue has been fixed. Earning me an acknowledgement.